Web Application Firewall, i.e. home page firewall. Zone now offers it and pays for trials, it will definitely make your website more secure!
WAF or Web Application Firewall
Most attacks against web pages exploit some weakness in the code, the most common of which are insufficient checks on user rights or data entered by the visitor.
For example, you could imagine a situation where entering the address in the ' OR 1=1;-- field on the utility company’s readings reporting page displays the addresses and previous readings of all customers… because that’s exactly what the database looks like, i.e. SQL injection. Or, a request is made to WordPress, which adds Javascript code that redirects visitors to the page through the settings of a plugin that does not check permissions.
Such code errors are also the reason why everything available on the public internet must be updated practically every day: every patched security problem brings a wave of scanners looking for vulnerable websites within 24 hours at the latest.
In addition, there are vulnerabilities that may not be fixed yet – because the developer is not aware of the problem, has not had time to patch it… or has been patched, but in a newer version, and transferring the web to it turns out to be labor-intensive.
img class=”alignright size-medium wp-image-5991″ src=”https://blog.zone.ee/static/sites/2/2019/08/CRS3-movie-poster-small-214×300 .jpg” sizes=”(max-width: 214px) 85vw, 214px” srcset=”https://blog.zone.ee/static/sites/2/2019/08/CRS3-movie-poster-small-214×300. jpg 214w, https://blog.zone.ee/static/sites/2/2019/08/CRS3-movie-poster-small-768×1075.jpg 768w, https://blog.zone.ee/static/sites/ 2/2019/08/CRS3-movie-poster-small-731×1024.jpg 731w, https://blog.zone.ee/static/sites/2/2019/08/CRS3-movie-poster-small.jpg 1200w” alt=”” width=”214″ height=”300″ />
Web Application Firewall
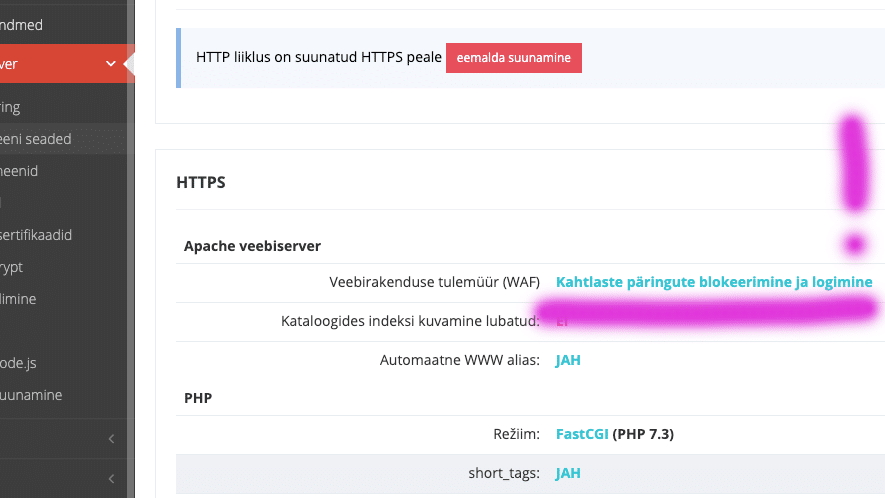
In such cases, a web application firewall, or WAF, can help, which tries to detect and block suspicious requests. Zone Virtual servers use ModSecurity and now you can also conveniently activate OWASP ModSecurity Core Rule Set (CRS)‘s firewall rules:
You can choose between logging or blocking and logging. If there is a plan and the ability to analyze the logs, then it is of course worth starting with logging and avoiding disturbing honest users with false-positive detections… But it is easier to turn on the blocking and test the functionalities.
In any case, we recommend checking that logs reaching the server in real time are also turned on .
In about 10 minutes, the setup will reach the Virtual Server, and if you then try to enter, for example, ' OR 1=1;-- in the WP search, the result should be Error403:
This results in the following lines in the /logs/apache.ssl.error.log file (cleaned up a bit for readability):
[2019-08-21 09:17:19.367098] [client 217.146.xx.x] ModSecurity: Warning. detected SQLi using libinjection with fingerprint 's&1;c' [file "REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "64"] [id "942100"] [data "Matched Data: s&1 ;c found within ARGS: ' OR 1=1;--"] [severity "CRITICAL"] [uri "/"] [unique_id "XVzh78ean2NKORtLccJqvgAAAAM"] [2019-08-21 09:17:19.367352] [client 217.146.xx.x] ModSecurity: Access denied with code 403 (phase 2). Inbound Anomaly Score Exceeded (Total Inbound Score: 5 - SQLI=5,XSS=0,RFI=0,LFI=0,RCE=0,PHPI=0,HTTP=0,SESS=0)
The log shows the reason (SQL or database injection), the rule number (942100), the data that triggered it, and also the